What's CRUD and Direct Secure Messaging got to do with streamlining workflow? Everything
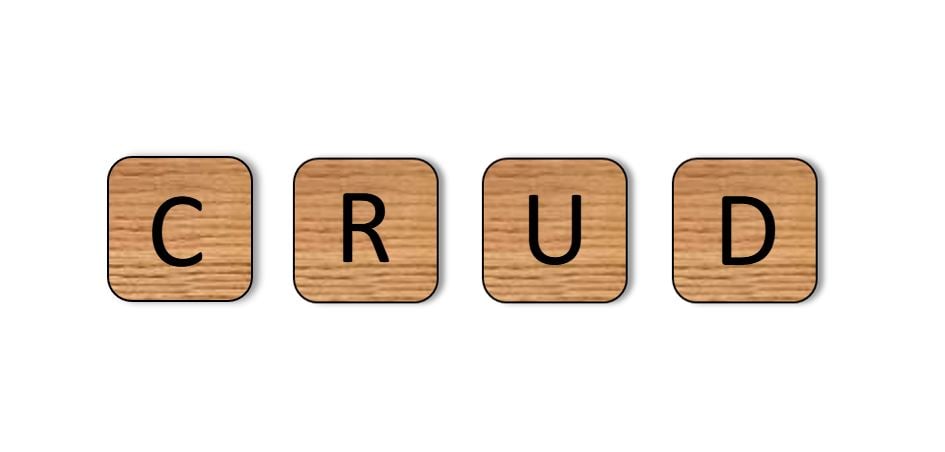
CRUD
CRUD is an acronym used in IT that stands for Create, Read, Update, and Delete. These functions are the essential functions that are necessary to create and maintain data in a database or data management system such as in EHR. In this post we discuss how patient data is kept updated in near real-time by using Direct Secure Messaging and CRU operations to create, read, and update Medical Records in an EHR system regardless of care setting, provider, or EHR system (see the next paragraph for a discussion of Delete).
Read More![iShareLogo-CircR-NoBG-150px[1] iShareLogo-CircR-NoBG-150px[1]](https://blog.isharemedical.com/hs-fs/hubfs/iShareLogo-CircR-NoBG-150px%5B1%5D.png?width=331&height=150&name=iShareLogo-CircR-NoBG-150px%5B1%5D.png)